Cybersecurity Gaps and Compliance Regulatory Risk: The Material Enterprise Threat PE Firms Systematically Underestimate
Why PE firms spend 45% less on cyber diligence than technology diligence, and how this gap creates material post-close financial and regulatory exposure.
When a PE firm acquires a target company, it inherits not just an operating business but the entire portfolio of security vulnerabilities, regulatory compliance gaps, and cyber risk that has accumulated over the target’s operational history. A software company running unpatched systems from 2020, a healthcare provider storing patient data without encryption, a manufacturing business with weak access controls, or a financial services firm operating non-compliant data centers—all of these security postures migrate to the acquiring firm on Day 1.
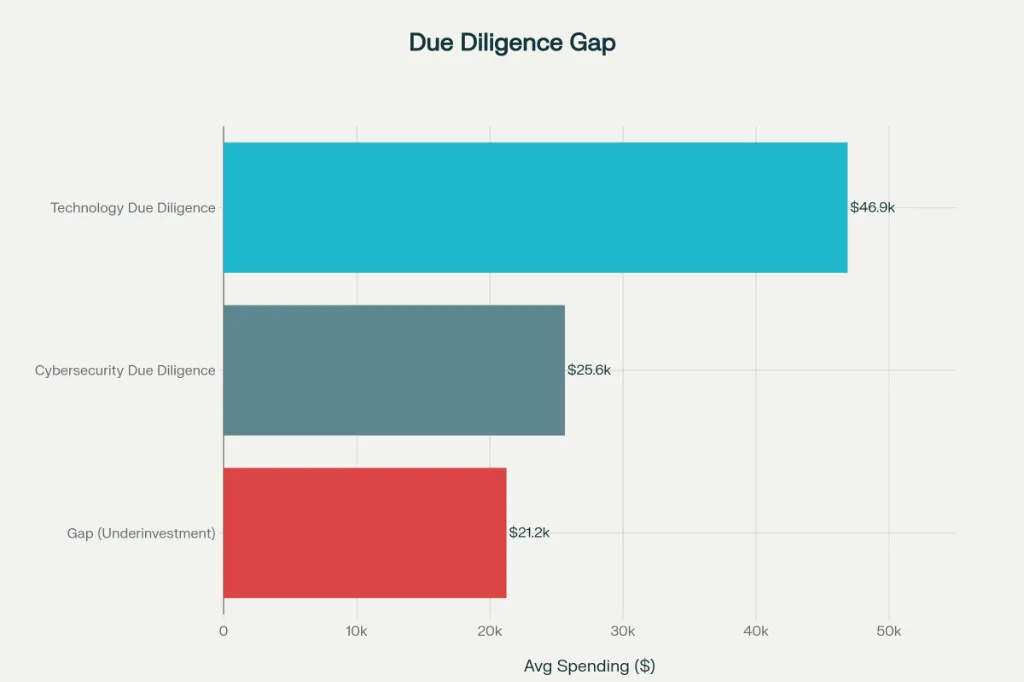
Yet PE firms systematically underinvest in cybersecurity assessment during acquisition due diligence. A 2025 S-RM survey of 100 PE professionals across multiple regions found that while 89% report cybersecurity maturity influences acquisition decisions, PE firms spend an average of only $25,630 on cybersecurity due diligence per deal—less than half the $46,875 spent on technology due diligence more broadly. This represents a 45% diligence gap on the very issues that create the highest post-close financial and legal exposure.
The consequences are severe. A data breach at an acquired company costs an average of $4.45M in direct costs, but the inherited regulatory liability, reputational damage, and deal value destruction often exceed $10-50M. For a PE firm targeting 3-4x returns on a $200M acquisition, a $15-25M post-close cyber incident effectively eliminates all projected value creation. Yet 53% of PE firms discover critical security issues only after deal close, and 62% of M&A deals experience delays caused by post-discovery cybersecurity problems.
This article deconstructs the cybersecurity gaps and compliance regulatory risks that PE acquisitions systematically overlook: why security assessment remains underweighted in due diligence despite material financial exposure, what specific security vulnerabilities create the highest risk, how unpatched systems expose firms to regulatory penalties, what third-party vendor compromise means for portfolio risk, and how to integrate cybersecurity into PE decision-making to transform cyber risk from a value destroyer into a value-creation lever.
Why Cybersecurity Remains the Blind Spot in PE Due Diligence
The Fundamental Diligence Imbalance
PE firms conduct due diligence on 70% of acquisitions, spending an average of $4-8M on financial, legal, operational, and technology assessment per deal. Yet cybersecurity—arguably the highest-risk operational component—receives less than 1% of that diligence budget.
The reason is structural: cybersecurity assessment requires specialized expertise that most PE investment teams lack. A financial due diligence team excels at assessing revenue quality, cost structure, and working capital. Operational due diligence teams can evaluate supply chain, manufacturing efficiency, and customer satisfaction. Technology due diligence teams can assess software architecture and development practices. But cybersecurity assessment requires specific expertise in:
- Network penetration testing and external exposure mapping
- Vulnerability scanning and patch management assessment
- Incident response procedures and breach history validation
- Regulatory compliance assessment (GDPR, HIPAA, SOC 2, ISO 27001, etc.)
- Vendor security evaluation
- Forensic analysis if prior breaches occurred
Most PE firms don’t maintain this expertise in-house. Engaging external cybersecurity experts adds cost, extends timelines, and requires PE teams to have language to brief boards on risks they often don’t fully understand. When timelines compress—which they invariably do in competitive deal environments—cybersecurity assessment gets deprioritized in favor of financial, legal, and operational due diligence.
The result: a systematic information asymmetry where sellers (who know the target’s security posture intimately) have strong incentive to minimize cyber risk disclosure, while buyers lack the expertise to assess it independently. This creates the classic market for lemons dynamic where security vulnerabilities remain invisible until post-close.
The Time and Budget Squeeze
PE diligence typically occurs in a 6-12 week window. Within that window, deal teams must assess financials (2-3 weeks), legal (2-3 weeks), operations (2-3 weeks), and technology (1-2 weeks). Cybersecurity—if conducted at all—competes for time within the technology due diligence window.
Given this time constraint, deal teams prioritize items that directly impact deal financing or near-term legal liability. Cybersecurity gets squeezed because:
- It’s not immediately visible: A company can operate for years with significant security vulnerabilities without experiencing a breach. A CFO reviewing financial controls can identify weaknesses immediately; a cybersecurity gap may remain dormant.
- It requires post-close remediation investment: Addressing security gaps costs capital (estimated $500K-$5M depending on severity). Deal teams building financial models often treat this as a “post-close issue” rather than deal economics.
- It’s difficult to quantify: Financial teams can calculate the cost of a quality issue or customer concentration risk. Cybersecurity risk—the probability and magnitude of a breach—is inherently uncertain, making it difficult to model precisely.
- It extends timelines: Comprehensive cybersecurity assessment can extend diligence by 3-4 weeks. In competitive deal environments, this timeline extension can cost the deal to another bidder.
The cumulative effect: PE teams knowingly reduce cybersecurity due diligence depth to accelerate deal closing, accepting the risk that material security gaps will emerge post-close.
The Seller Incentive Problem
Sellers have strong incentive to minimize cybersecurity risk disclosure. A target company’s valuation typically incorporates 7-8x EBITDA. If cybersecurity gaps emerge during diligence, they create multiple headwinds:
- Valuation reduction: Identified security gaps trigger renegotiation and price reduction
- Earnout reduction: If the deal structure includes earnout provisions, security gap remediation reduces available cash flow
- Timeline extension: Addressing security gaps delays closing and extends working capital
- Deal risk: In extreme cases, material security gaps can trigger deal termination
Given these incentives, sellers often:
- Minimize disclosed breach history (not voluntarily mentioning near-misses or security incidents that didn’t escalate to breaches)
- Downplay the extent of unpatched systems or outdated technology
- Characterize security gaps as “normal” for the industry rather than material
- Hide compliance gaps that would trigger regulatory penalties if discovered
Without sophisticated cybersecurity assessment, PE buyers cannot independently verify seller representations about security posture. A company’s management can credibly claim “our security is solid” without buyers having the expertise to challenge this claim.
The Hidden Vulnerabilities: What Cybersecurity Due Diligence Actually Finds
When PE firms do engage serious cybersecurity assessment, common findings include:
Vulnerability 1: Pervasive Unpatched Systems
Organizations should apply critical security patches within 30 days. Yet research shows that 32% of critical vulnerabilities remain unpatched for over 180 days. For acquired companies—often running legacy systems with limited IT resources—patch management is frequently ad hoc or non-existent.
A typical finding: A middle-market software company running on Windows Server 2012 (end-of-support: October 2023) with dozens of critical security patches missing. The company’s IT team consists of two people managing infrastructure and applications across 50+ systems. Prioritizing patch management never surfaced as a project because infrastructure problems kept IT in reactive mode.
Financial Impact:
- Unpatched systems create known exploitable vulnerabilities
- A breach exploiting an unpatched vulnerability can trigger regulatory fines (regulators expect reasonable patching discipline)
- Median time from vulnerability disclosure to exploitation: less than 48 hours for critical vulnerabilities
- Average breach exploitation cost: $4.45M in 2024
Regulatory Impact:
- GDPR violations for inadequate security controls: up to €20M or 4% of revenue
- HIPAA violations for unpatched systems accessing PHI: $100-$50,000 per patient record exposed
- SOC 2 non-compliance: prevents partnership integrations and enterprise sales
Vulnerability 2: Missing Compliance Certifications
Enterprise customers increasingly require security certifications as conditions for partnerships or data sharing. Common requirements include:
- SOC 2 Type II: Demonstrates security controls operating effectively over 6-12 months. Cost to achieve: $35K-$100K; timeline: 12-18 months
- ISO 27001: International information security management standard. Cost: $50K-$150K; timeline: 12-18 months
- HIPAA compliance: For healthcare companies. Cost: $100K-$500K depending on system complexity; timeline: 6-24 months
- GDPR readiness: For companies processing EU resident data. Cost: $50K-$200K; timeline: 3-12 months
A typical finding: A SaaS company targeting enterprise customers has 15 major customers requiring SOC 2 certification. The company has implemented security controls but has never pursued formal attestation. Pursuing SOC 2 now would require 12-18 months and $50-100K in consulting costs. Without SOC 2, the company cannot expand enterprise sales.
Financial Impact:
- Lack of SOC 2 blocks enterprise customer acquisition (estimated $1-5M in blocked annual revenue)
- Achieving SOC 2 requires capital investment ($50K-$100K) competing with product development
- Revenue growth targets become unattainable without certification
Vulnerability 3: Weak Access Controls and Identity Management
Many acquired companies operate without multi-factor authentication (MFA), segregation of duties, or privileged access management (PAM). Access control weaknesses create two problems: (1) insider threat risk, and (2) external attacker exploitation.
A typical finding: A healthcare company’s EHR system allows any employee to access any patient’s records. The company has no audit logging of who accessed which records or when. An employee accidentally emails patient data to the wrong recipient. The company’s incident response process doesn’t exist—management doesn’t discover the incident for three weeks when a patient reports it.
Financial Impact:
- HIPAA breach notification costs: $1,000-$50,000 per exposed record
- A 10,000-record exposure in this scenario: $10M-$500M liability
- Regulatory investigation costs: $500K-$2M
- Reputation damage and patient attrition
Vulnerability 4: No Incident Response Program
Many smaller companies lack formal incident response procedures. When a breach occurs, the company muddles through—attempting to figure out what data was compromised, whether to notify regulators, whether to involve law enforcement or forensic investigators.
A typical finding: A manufacturing company discovers suspicious network activity suggesting a breach. The company has no incident response plan, no forensic investigator on retainer, and no designated breach response leader. The company spends three months attempting to investigate internally, during which the attacker completes data exfiltration. By the time external forensic investigators are engaged, critical evidence is lost. The incident response timeline extends from days to months.
Financial Impact:
- IBM’s 2025 Cost of a Data Breach Report: Organizations containing breaches within 200 days save over $1M compared to organizations taking longer
- Typical incident response cost for a managed breach: $500K-$2M
- Unmanaged response cost: $5M-$15M+ as remediation extends and regulatory penalties accumulate
Vulnerability 5: Vendor and Supply Chain Risk
Many companies rely on critical vendors without assessing their security. A compromised vendor becomes an entry point to the target company.
A typical finding: A PE-backed manufacturing company relies on a third-party logistics provider for order management and inventory. The logistics provider uses cloud infrastructure with weak identity controls. An attacker compromises the logistics provider’s infrastructure, gaining access to the manufacturing company’s sales orders, customer information, and supplier relationships. The compromise remains undetected for six weeks because the manufacturing company has no vendor risk monitoring.
Financial Impact:
- Supply chain compromises cost an average of $4.91M and take longer to identify than other breaches
- Breach detection delays: 204 days average to detect a breach; 73 days to contain
- Revenue impact: Supply chain compromise disrupts operations, prevents order fulfillment, customer delivery delays
Vulnerability 6: Legacy Technology and End-of-Life Systems
Many acquired companies operate on systems approaching or past end-of-support dates. Vendors discontinue security updates for end-of-life systems, leaving them permanently vulnerable.
A typical finding: A healthcare company runs on SAP version 4.6c (released 1998, end-of-support 2005). The system is no longer receiving security patches. The company has 400+ customizations making migration to modern systems extraordinarily complex and expensive.
Financial Impact:
- System modernization cost: $3-10M depending on customization complexity
- Timeline: 18-36 months
- Regulatory risk: Regulators increasingly scrutinize organizations operating unsupported systems
The Financial Impact: Quantifying Cybersecurity Breach Risk
For PE decision-makers evaluating cyber risk, financial quantification requires understanding breach costs across three dimensions:
Direct Breach Costs
Average breach costs by scenario:
| Breach Type | Low Estimate | High Estimate | 2024 Industry Data |
|---|---|---|---|
| Data breach (small) | $1M | $3M | $4.45M avg |
| Ransomware incident | $2M | $8M | $5.08M avg |
| Supply chain breach | $3M | $15M | $4.91M avg |
| Regulatory-triggered breach | $5M | $50M | Varies by regulation |
These direct costs include:
- Incident response and forensic investigation: $300K-$2M
- Breach notification and credit monitoring: $200K-$1M
- Legal fees and regulatory defense: $500K-$3M
- Regulatory fines and penalties: $0-$50M+ depending on regulation and breach scope
Indirect Costs and Value Destruction
Beyond direct costs, breaches create substantial indirect financial impact:
Downtime and operational disruption:
- Ransomware incidents average $1.53M in recovery costs excluding ransom
- Manufacturing/operations companies experience production loss: $10K-$100K per hour depending on facility size
- A 48-hour ransomware recovery for a manufacturing company: $500K-$5M in lost production
Reputational damage and customer attrition:
- Customer trust loss typically results in 15-30% customer churn in following 12 months
- For a SaaS company with $50M ARR and 5% annual churn, a breach-triggered additional 10% churn = $5M revenue loss
- Customer acquisition cost increases 20-40% post-breach due to heightened customer skepticism
Regulatory and compliance costs:
- GDPR fines: €20M or 4% of global revenue (whichever is higher)
- HIPAA fines: $100-$1.5M per violation, with violations sometimes numbering in hundreds
- SOC 2 mandatory remediation: $50K-$200K plus 12-18 month timeline extension
Deal value destruction:
- Acquirer MOIC reduction from discovered security gaps: 15-30% valuation adjustment
- Earnout clawbacks if security incident occurs during earn-out period
- Extended exit timelines if security remediation required pre-sale
Portfolio-Level Risk Aggregation
For PE firms managing multiple portfolio companies, cyber risk aggregates:
Typical PE portfolio with 10 companies:
| Risk Metric | Portfolio Impact |
|---|---|
| Probability 1+ company experiences breach in 12 months | 65-75% |
| Expected aggregate breach cost (probability-weighted) | $2-5M |
| Expected regulatory investigation/fine cost | $1-3M |
| Reputational spillover impact (LP confidence) | Unquantifiable but material |
For a PE fund managing $1B AUM, a major cyber incident at a portfolio company reducing LP confidence by 5% translates to $50M in potential capital reduction in next fund formation.
The Regulatory Landscape: When Security Gaps Trigger Penalties
Regulatory bodies increasingly view cybersecurity and data protection as enforceable obligations. PE firms acquiring companies with compliance gaps inherit the regulatory liability.
GDPR: The $20M+ Risk
GDPR applies to any company processing personal data of EU residents, regardless of where the company is located. Violations trigger fines of €20M or 4% of global revenue (whichever is higher).
Common GDPR violations discovered in acquisitions:
- No privacy policy or inadequate disclosure of data collection/processing
- No data subject consent for processing
- Inadequate data retention policies (data kept longer than necessary)
- No vendor privacy agreements when processing data with third parties
- Inadequate security controls on personal data
- No data breach response or notification procedures
Real-world example: Marriott’s 2018 acquisition of Starwood Hotels inadvertently created a GDPR violation when Marriott inherited Starwood’s customer database containing millions of EU residents’ personal data. After a breach in Starwood’s system exposed the data, Marriott was fined £99 million ($110M USD) for GDPR violations—an acquisition-inherited liability that predated Marriott’s acquisition.
HIPAA: The $50K-per-record Risk
For healthcare companies, HIPAA violations create per-record liability. A breach of 100,000 patient records could trigger $5M-$500M in potential fines depending on violation type.
Common HIPAA violations in acquired healthcare companies:
- Inadequate encryption of patient health information (PHI)
- Missing business associate agreements with vendors processing PHI
- Inadequate access controls (employees accessing PHI they don’t need)
- Missing audit logs of who accessed PHI
- Inadequate physical security (unlocked equipment, unsecured facilities)
Real-world example: Advocate Medical Group paid $5.55M HIPAA settlement after a data breach involving an unencrypted laptop stolen from an employee’s vehicle. The company had failed to conduct adequate risk analysis, implement proper device safeguards, or establish vendor agreements.
SOC 2: The Enterprise Sales Blocker
While SOC 2 is not a regulatory requirement, it has become a de facto market standard for enterprise software companies. 87% of PE firms now mandate SOC 2 compliance for their service providers.
Impact of missing SOC 2:
- Blocks enterprise customer deals (estimated 25-50% of potential TAM in enterprise-focused SaaS companies)
- Requires 12-18 months to achieve (Type II)
- Costs $35K-$100K in consulting to implement
- Ongoing compliance maintenance cost: $10K-$30K annually
For a SaaS company targeting $50M ARR, the inability to pursue enterprise customers due to missing SOC 2 represents $10-25M in lost annual revenue opportunity.
Vendor and Third-Party Risk: The Supply Chain Vulnerability
PE firms often overlook that acquired companies’ cybersecurity posture depends critically on vendors and third parties. A breach at a critical vendor becomes a breach of the acquired company.
The Supply Chain Attack Mechanism
A third party (vendor, software provider, logistics partner) is compromised by attackers. The attacker gains access to the third party’s systems and customer data. The acquired company, which relies on the third party, becomes compromised as collateral damage.
Real-world examples:
- SolarWinds Supply Chain Attack (2020): Attackers compromised SolarWinds’ software development system, injecting malicious code into SolarWinds Orion platform updates. When customers deployed the updates, they unwittingly downloaded malicious code. Over 18,000 organizations were affected, including dozens of Fortune 500 companies and multiple U.S. government agencies. The attack exploited a supply chain dependency that customers had no visibility into.
- MOVEit Transfer Vulnerability (2023-2025): A zero-day vulnerability in Progress MOVEit Transfer (file transfer software) affected 2,000+ organizations. Attackers exploited the vulnerability to access sensitive HR and finance data. Organizations relying on MOVEit Transfer became compromised without awareness of the underlying vulnerability. Once disclosed, attackers exploited the vulnerability within hours.
- Blue Yonder Supply Chain Disruption (2024): Ransomware attack on Blue Yonder disrupted operations at Starbucks, UK grocery chains, and hundreds of other companies relying on Blue Yonder supply chain software. The ripple effect illustrated how supplier compromise creates cascading operational impact.
Financial Impact of Supply Chain Compromise
- Detection time: 204 days average before detection
- Containment time: 73 additional days after detection
- Cost: $4.91M average, exceeding single-entity breaches
- Operational impact: Disruption extends across all connected entities
- Regulatory liability: Customers of the compromised company may hold the company liable for their own breach exposure
For a PE-backed company relying on a critical vendor, vendor compromise creates financial impact exceeding typical breach costs because the company must (1) remediate its own systems, (2) notify customers, (3) engage in legal defense, and (4) manage reputational damage from both the company’s own vulnerability and its vendor’s vulnerability.
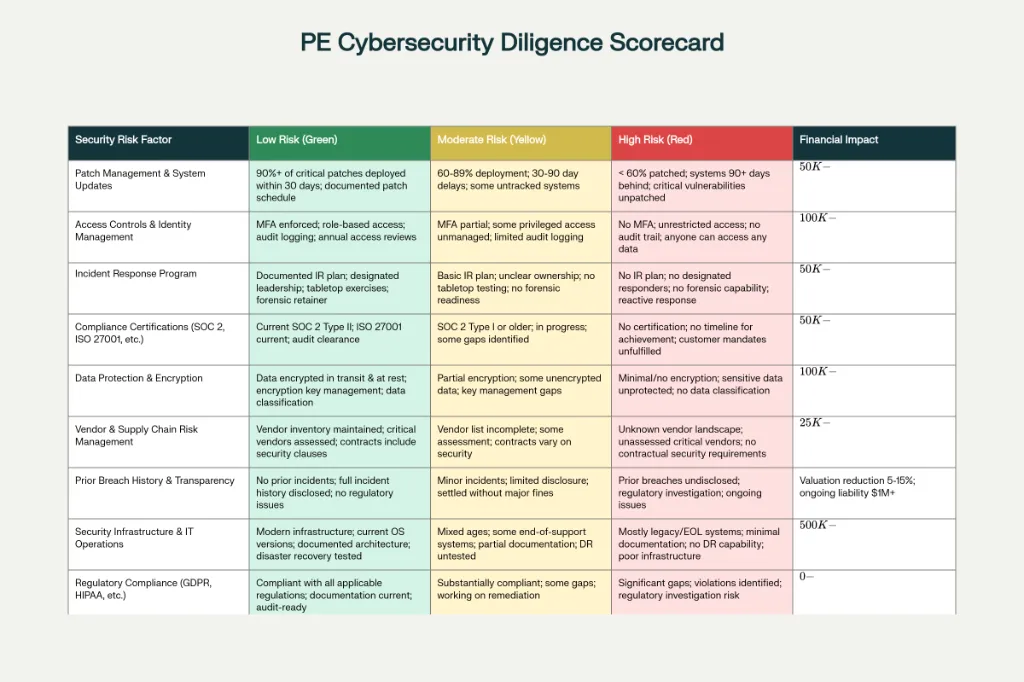
Assessment Framework: Identifying Cybersecurity Risk During Due Diligence
For PE firms integrating cybersecurity into acquisition decisions, a structured assessment framework should include:
Phase 1: Rapid Cyber Risk Screening (Week 1-2)
Activities:
- External exposure assessment: Identify the target company’s externally visible systems (web applications, APIs, cloud infrastructure) and known vulnerabilities
- Vendor risk screening: Identify critical vendors and assess their security profile
- Regulatory compliance screening: Determine applicable regulations (GDPR, HIPAA, SOC 2, etc.) and assess compliance status
- Breach history research: Search public databases for disclosed breaches involving the target company
- Technology stack assessment: Identify whether systems are on current versions or end-of-support
Output: High-level cyber risk profile; identified high-risk areas requiring deeper investigation Cost: $15K-$30K; Timeline: 1-2 weeks
Phase 2: Deep Technical Assessment (Week 3-5)
For higher-risk targets identified in Phase 1:
- Vulnerability scanning: Comprehensive scan of target’s infrastructure, applications, and systems for known vulnerabilities
- Incident response assessment: Review existing incident response procedures, breach history, and incident management capabilities
- Compliance gap assessment: Detailed review of compliance requirements and existing gaps
- Vendor due diligence: Detailed assessment of critical vendors’ security posture
- Security control evaluation: Review access controls, identity management, data protection, encryption, and monitoring
Output: Detailed technical risk report; prioritized remediation roadmap; cost estimates for remediation Cost: $50K-$150K; Timeline: 3-5 weeks
Phase 3: Regulatory and Legal Assessment (Week 5-6)
Activities:
- Regulatory compliance review: Assess current compliance status with applicable regulations
- Prior breach assessment: Review any prior security incidents and regulatory responses
- Vendor contract review: Assess adequacy of vendor security requirements and liability provisions
- Customer contractual exposure: Review customer contracts for security and compliance obligations
Output: Identified compliance gaps; quantified regulatory exposure; contractual liability assessment Cost: $20K-$50K; Timeline: 1-2 weeks
Phase 4: Financial Modeling (Week 7+)
Integrate findings into financial models:
- Cyber remediation cost estimates: Budget for security gap remediation
- Regulatory penalty scenario modeling: Estimate potential regulatory exposure
- Post-breach operational impact modeling: Model revenue impact of potential breach
- Insurance analysis: Evaluate cyber insurance costs and coverage gaps
Output: Revised acquisition thesis accounting for cyber risk; adjusted financial projections Cost: Included in broader financial diligence; Timeline: 1-2 weeks
Red Flags: When Cybersecurity Risk Should Trigger Deal Reconsideration
Certain findings should raise serious concerns about cybersecurity risk:
Red Flag 1: Prior Undisclosed Breaches If investigation uncovers prior security incidents that management did not disclose, this signals material asymmetric information. The question becomes: what other security issues are being hidden?
Red Flag 2: Extensive Unpatched Systems If the target company has more than 10-15% of its systems on outdated versions with known critical vulnerabilities, remediation will require substantial investment and extended timeline.
Red Flag 3: No Incident Response Program If the target company has no documented incident response procedures and no designated breach response leadership, the company will be reactive post-breach, increasing costs and extending timelines.
Red Flag 4: Missing Compliance Certifications in Enterprise-Focused Business If an enterprise-focused SaaS company lacks SOC 2, the company cannot pursue enterprise customers regardless of product quality.
Red Flag 5: Vendor Concentration Without Vendor Risk Management If the target company depends on 2-3 critical vendors without assessing their security posture or contractual protections, supply chain compromise creates material operational risk.
Red Flag 6: Inadequate Security Controls (No MFA, No Encryption, Weak Access Controls) Basic security controls (MFA, encryption, access management) are non-negotiable. Their absence indicates fundamental security immaturity that will require substantial investment to remediate.
Recommendations for PE Firms
1. Establish Mandatory Cyber Assessment for All Acquisitions >$50M
Rather than treating cybersecurity as optional due diligence, make it a required component for all material acquisitions. For smaller acquisitions, implement rapid cyber screening (Phase 1) to identify whether deeper assessment is warranted.
Budget: $25K-$50K for rapid screening; $75K-$200K for detailed assessment Timeline: 2-5 weeks ROI: Prevents $5-50M in post-close cyber surprises
2. Hire or Retain Dedicated Cyber Due Diligence Expertise
Either develop internal cybersecurity expertise or establish retainer relationships with specialized cyber firms capable of conducting rapid, decision-quality assessments. Internal expertise enables better integration of cyber considerations into portfolio management.
3. Adjust Acquisition Multiples for Cyber Risk
Rather than treating cybersecurity gaps as post-close “nice-to-haves,” incorporate cyber risk into valuation adjustments:
Sample framework:
- Strong cyber posture (SOC 2 certified, current systems, incident response program): Full valuation
- Moderate cyber risk (missing SOC 2, some unpatched systems, basic controls): 3-5% valuation reduction
- High cyber risk (extensive unpatched systems, regulatory gaps, no incident response): 5-10% valuation reduction
- Critical cyber risk (prior breaches, major compliance violations, fundamental security failures): 10-20% reduction or deal decline
4. Incorporate Cyber Remediation into First-Year Operating Plan
Rather than deferring security investments to later years, budget for critical remediation in Year 1:
- SOC 2 certification: $50K-$100K + 12-18 month timeline
- Unpatched systems remediation: $100K-$500K + 3-6 month timeline
- Incident response program build: $50K-$150K
- Vendor risk management program: $25K-$75K
5. Establish Cyber Insurance Strategy
Cyber insurance serves as a risk transfer mechanism but cannot substitute for sound security practices. Evaluate insurance needs:
- Minimum annual cyber insurance: $500K-$2M depending on revenue and data sensitivity
- Ransomware coverage explicit: $500K-$5M sub-limits
- Regulatory penalty coverage: $1M-$5M depending on regulatory exposure
6. Build Cybersecurity KPIs into Portfolio Monitoring
After acquisition, track cybersecurity metrics alongside operational KPIs:
- Patch management: Percentage of critical vulnerabilities patched within 30 days (target: 90%+)
- Incident detection: Time from incident occurrence to detection (target: <7 days)
- Compliance status: Certifications current and maintained (SOC 2, ISO 27001, HIPAA, etc.)
- Vendor security: Percentage of critical vendors with current security assessments (target: 100%)
- Employee training: Annual cybersecurity training completion rate (target: 90%+)
Conclusion: Cybersecurity as a Value Creation Lever
The PE firms that will outperform peers in software and services acquisitions are those that integrate cybersecurity into deal decision-making rather than treating it as an optional add-on. The financial stakes are too high—a $15-50M cyber incident or regulatory penalty can easily erase 15-30% of projected acquisition returns.
For Operating Partners, portfolio company CFOs, and investment professionals responsible for deal evaluation, the imperative is clear: cybersecurity is not a technical concern delegated to IT—it is a fundamental business and financial risk that requires Board-level attention during diligence and materiality assessment during valuation.
The firms recognizing cybersecurity as a value creation lever will systematically identify security gaps during diligence, adjust valuations appropriately, budget for remediation in operating plans, and monitor cyber metrics alongside operational KPIs. These firms will avoid the value destruction that arises from cyber surprises, regulatory penalties, and reputational damage.
For the PE firms still treating cybersecurity as a secondary due diligence item, the competitive advantage being ceded is substantial. As regulatory scrutiny increases, breach costs escalate, and LPs increasingly weight cyber risk management in manager evaluation, the firms underweighting cybersecurity will find themselves at a persistent disadvantage relative to peers who have made it central to investment decision-making.
References and Source Data
- S-RM survey of 100 PE professionals; 89% report cybersecurity influences decisions but spend $25,630 on cyber DD vs. $46,875 on technology DD (2025)
- Average cost of data breach: $4.45M in 2024 (uzado.com, 2025); ransomware average $5.08M; supply chain average $4.91M
- IBM Cost of a Data Breach Report 2025; WTW Cyber Claims Analysis reporting average ransom demand USD 5M
- 53% of PE firms discover critical security issues post-close; 62% experience M&A delays from cyber issues (industry data compilation)
- 32% of critical vulnerabilities remain unpatched for over 180 days; 115 CVEs disclosed daily in Q4 2024 (Security Boulevard, 2024)
- GDPR fines: up to €20M or 4% of revenue; SOC 2 denial of enterprise sales; ISO 27001 market requirements
- SOC 2 achievement costs $35K-$100K; timeline 12-18 months; 87% of PE firms mandate SOC 2 for service providers (Guru Startups, 2025)
- ISO 27001 implementation costs and timelines (industry estimates)
- IBM Cost of a Data Breach Report 2025: 204 days to detect breach, 73 days to contain; organizations containing within 200 days save $1M+
- Supply chain breach average cost $4.91M; takes longer to identify than other breaches (Mayer Brown, 2025)
- Ransomware recovery costs average $1.53M excluding ransom; $5.13M average total cost (PurpleSec, 2025)
- Marriott GDPR fine: £99M after Starwood Hotel acquisition breach (£99M = ~$110M USD); Verizon Yahoo acquisition: $350M price reduction from disclosed breaches
- Advocate Medical Group HIPAA settlement: $5.55M for unencrypted laptop breach (SecureFrame, 2025)
- 87% of PE firms mandate SOC 2 for service providers; 78% of CPA firms report SOC 2 requests from PE clients (NOC Technology, 2025)
- SolarWinds supply chain attack (2020): 18,000 organizations affected; MOVEit vulnerability (2023-25): 2,000+ compromised; Blue Yonder (2024): Ransomware disrupted Starbucks and retailers
- Additional sources: McKinsey PE Regulatory Report (2024); BCG Regulatory Climate for PE (2024); Tanium unpatched software risks; SecurityBoulevard CVE disclosure tracking (2024); Infosys Cybersecurity Due Diligence in M&A; PI Partners Cyber M&A Briefing (2025); QUISS PE Cybersecurity Risks (2025); WTW Cyber Claims Analysis (2024)
